RBAC
RBAC (Role-based access control) is only available in Streamvisor Enterprise edition.
RBAC allows you to define fine-grained permissions for your users. It is fundamental to secure your data and restrict who can access which resources.
By default, RBAC is disabled. This gives every user full access to all Pulsar resources and Streamvisor configurations.
To enable RBAC, ask your administrator to set the required configuration property.
Note that when RBAC is disabled, you are still able to define permissions, they are just not enforced.
There are two categories of permissions, platform permissions and resource permissions.
- Platform permissions: define who can manage Streamvisor configurations.
- Resource permissions: define who can interact with Pulsar resources.
Both kinds of permissions are assigned at group-level. To grant permissions to a user, you add him to the respective groups (see Manage Users & Groups).
Permissions are additive, meaning a user that is part of two groups, one with restricted access to a topic and one with full access to it, will have full access as a result.
To assign platform permissions, select Admin/Groups in the sidebar and open the detailed view of the group you want to edit permissions for.
The checkbox next to the permission enables or disables it.
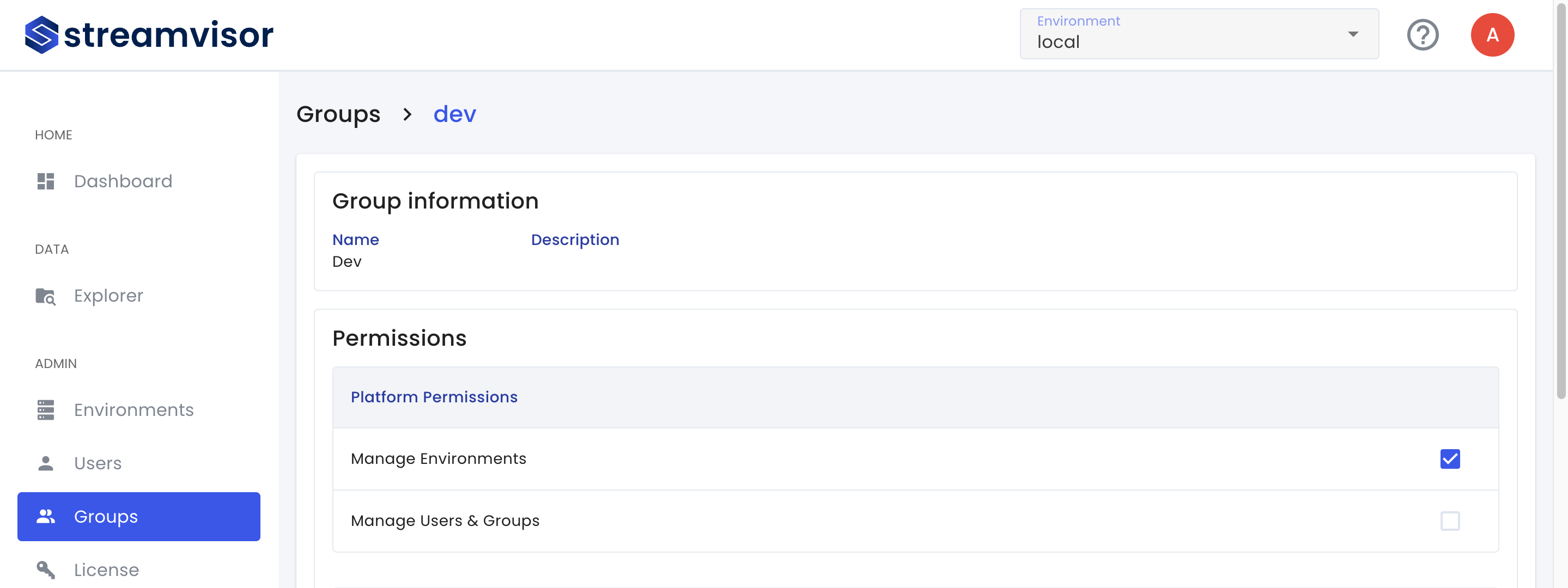
The platform permissions grant the following access:
- Manage Environments: Add, edit and delete environments
- Manage Users & Groups: Add, edit and delete users and groups
To assign platform permissions, select Admin/Groups in the sidebar and open the detailed view of the group you want to edit permissions for.
For each type of resource (tenant, namespace, topic) you can add permissions by clicking the Add Permission button.
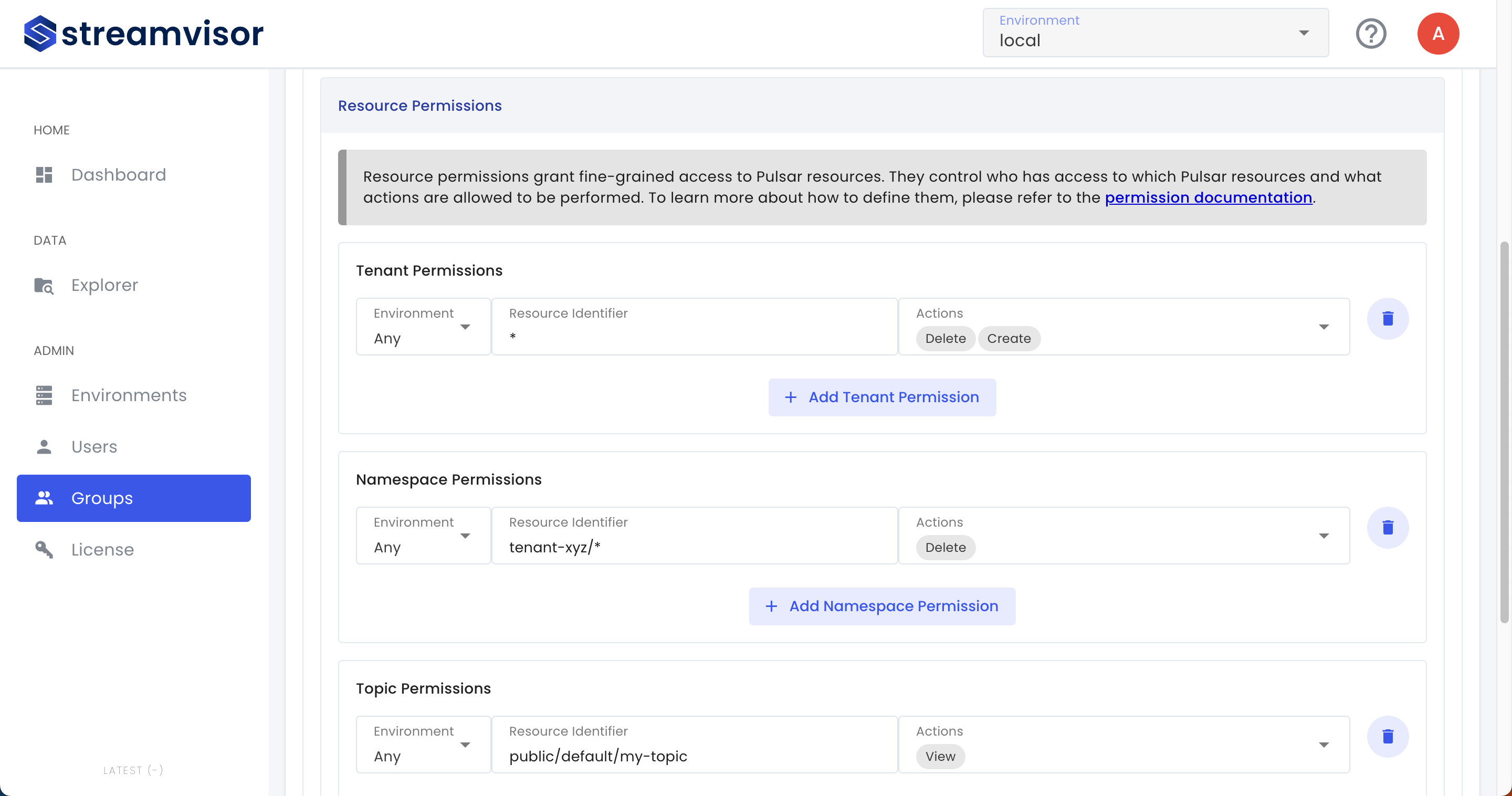
Each permission consists of three parts, the environment, the resource identifier and the actions. They denote the following:
- Environment: Select which environment the permission applies to (or ‘Any’ to apply to all)
- Resource Identifier: Identifies the Pulsar resource the permission applies to (See resource identifier syntax)
- Actions: Select which actions to the resource the permission will grant
The resource identifier syntax allows you to identify resources with some flexibility. Below you can find the allowed types of rules:
| Resource Identifier Example | Applies To |
|---|---|
*/*/* |
Everything - In any tenant, in any namespace, any topic |
demo/*/* |
In the demo tenant, in any namespace, any topic |
demo/crm/* |
In the demo tenant, in the crm namespace, any topic |
demo/crm/payments-* |
In the demo tenant, in the crm namespace, any topic starting with payments-* |
demo/crm/payments-us |
In the demo tenant, in the crm namespace, only the payments-us topic |